Why your Supply Chain Needs Role Based Access Control (RBAC)
Modern supply chains are the engines of global commerce, but they also present a growing security challenge. These complex networks, reliant on information exchange between multiple organizations, create a multitude of vulnerabilities. Unauthorized access to data can disrupt operations, lead to compliance issues, and erode customer trust.
The challenge lies in finding the right balance. Overly restrictive access controls can slow down operations and hinder collaboration. On the other hand, lax security measures open the door to a range of threats. So, how can organizations ensure efficient workflows while safeguarding sensitive data?
The answer lies in a powerful tool called Role-Based Access Control (RBAC). Imagine it as a way to grant access based on specific roles within the supply chain. A procurement manager needs different information than a warehouse worker, and RBAC ensures each gets exactly what they need to do their job effectively, without compromising security.
What is Role-Based Access Control (RBAC)?
Role-based access control (RBAC) is a security approach that authorizes and restricts system/network/resource access to users based on their organizational roles and responsibilities. Consider an organization with a complex supply chain. RBAC ensures that every stakeholder, from the CEO to the warehouse worker involved in the system, has access to the information needed to do their job effectively while preventing unauthorized access to sensitive data.
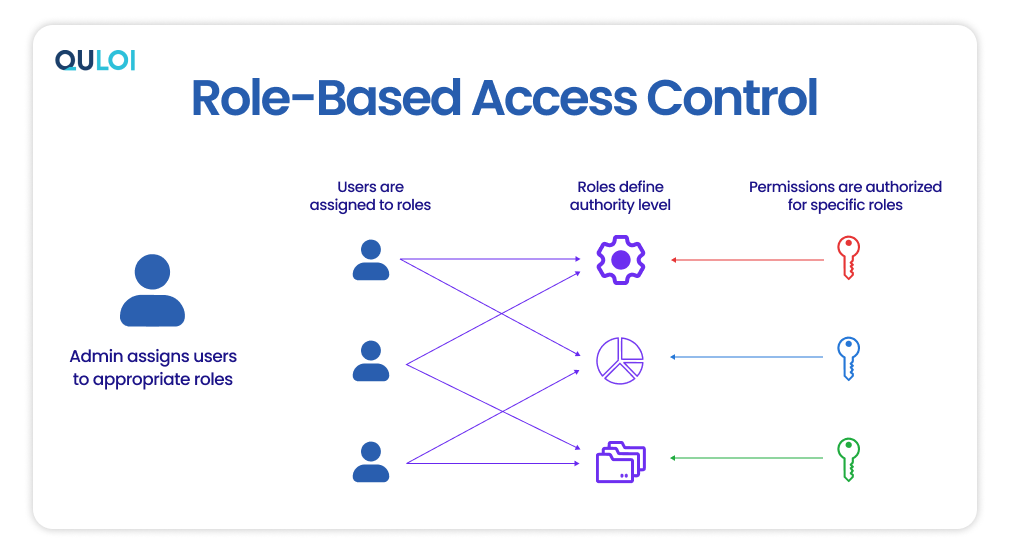
Examples of RBAC
Imagine you’re the logistics manager for an organization that sells laptops. Your role involves coordinating the smooth flow of laptops from factories to distribution centers and ultimately, store shelves. RBAC will ensure that you would have access to all information and systems related to critical logistics systems, including shipment schedules, transportation routes, and real-time inventory levels. However, you wouldn’t have access to sensitive financial data or customer information, which is only accessible to authorized roles like finance managers or customer service representatives.
Why is Role-Based Access Control Important in Supply Chain?
Purchase Order Management
While creating a purchase order, RBAC enables authorized access to procurement managers or authorized personnel to access and modify order details. This prevents unauthorized changes to POs, reducing the risk of fraud and ensuring a smooth purchasing process.
Booking
RBAC controls access to booking platforms, allowing designated buyers to make bookings for the transportation of products. This prevents unauthorized bookings, minimizes scheduling conflicts, and helps in efficient resource allocation.
Shipment Tracking
With RBAC, only authorized personnel, such as logistics managers or customer service representatives, can track the shipment status, communicate with freight forwarders, or update delivery information. This maintains the confidentiality and security of sensitive shipment data throughout transit.
Components of Role-Based Access Control
Role-based access control is based on key components determining user interactions and the resource, system, or process they are trying to access. While the list of components may vary across supply chains in organizations, here are the four foundational ones you need to remember.
Users: These are the individuals who need access to information and systems within your supply chain network. Think of employees, partners, and any other authorized users.
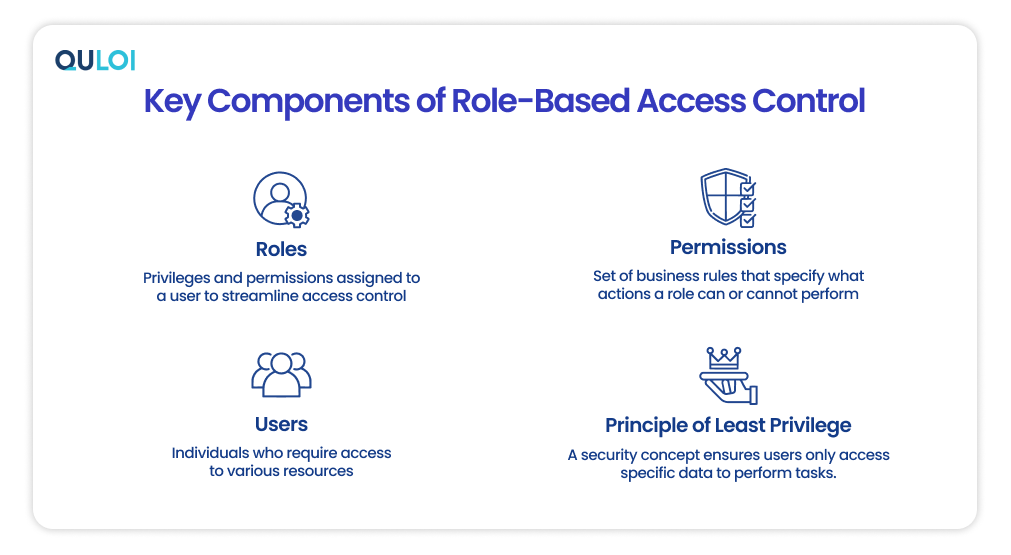
Roles: Imagine roles as job descriptions translated into access permissions. A procurement manager has different access needs than a warehouse worker, and RBAC defines these roles with specific permissions.
Permissions: These are the specific actions a user can perform within the system based on their assigned role. A logistics manager might have permission to view shipment schedules, but not edit financial data.
Principle of Least Privilege: This is the golden rule of RBAC. It dictates that users are granted the minimum level of access necessary to perform their assigned tasks.
How Can Supply Chains Benefit From RBAC?
Streamlined Collaboration: RBAC fosters collaboration by enabling supply chain partners to work together and managing who can access shared resources and platforms. RBAC manages access to a centralized supply chain management platform in a supply chain network, allowing manufacturers, suppliers, and distributors to collaborate on orders, shipping, and inventory management. This promotes open communication, transparency, and efficiency across the supply chain.
Security Enhancement: RBAC enhances security within the supply chain by ensuring that only authorized users access sensitive information or applications. For instance, RBAC would restrict access to machinery control users to trained professionals in a manufacturing facility. This prevents unauthorized users from tampering with equipment and protecting personnel and assets.
Compliance Adherence: RBAC supports compliance by enforcing access and audit trails for regulatory requirements. With RBAC, you can regulate access to customs declaration systems, ensuring that only licensed or authorized customs brokers can submit import/ export documentation. This minimizes the risk of costly non-compliance penalties or errors in customs processes, maintaining the integrity of cross-border trade operations. As Benjamin Franklin said, “An ounce of prevention is worth a pound of cure.”
Efficient Resource Allocation: RBAC allows you to optimize resource allocation by assigning access permissions based on jobs and responsibilities. In a warehouse, you can ensure only inventory managers access inventory details to track stock levels, place orders, and manage logistics efficiently. By restricting access to those who need it, you can reduce delays and misplaced orders – resulting in streamlined workflows and higher productivity.
Risk Mitigation: Since data is exchanged across various stakeholders, there are higher chances of data leaks, which means missed business opportunities. RBAC mitigates the risk of data leaks or misuse by assigning access privileges based on job roles, responsibilities, and organizational hierarchies. When limited users have access to key information, you reduce the risk of data breaches and ensure compliance with privacy regulations like GDPR.
Best Practices to Implement RBAC
Role Definition: Start by defining roles and responsibilities corresponding to different supply chain functions and responsibilities, such as supplier, buyer, distributor, inventory manager, etc. Map out roles based on the principle of least privilege, determining what level of access each role needs to perform different tasks.
Regular Auditing: Regularly audit user roles and permissions to detect and prevent unauthorized or malicious access and identify and rectify any errors in the RBAC system. Remove or adjust rights for roles that are no longer relevant or have changed roles.
Centralized Access Control: Implement a centralized access control system to manage user roles and permissions across the supply chain network. Use robust authentication mechanisms, like multi-factor authentication, to verify users’ identities before granting access to sensitive resources.
Training and Awareness: Train and educate users and administrators on RBAC policies and procedures. Ensure they understand their roles, permissions, responsibilities, and policies regarding access control and data security. This can help reduce the risk of potential human errors or misuse of the RBAC system.
Regular Updates and Maintenance: Update RBAC policies and access control mechanisms and evaluate their performance. Evaluation can involve reviewing and revising roles, permissions, policies, and systems and incorporating new technologies.
Limitations of RBAC
While RBAC offers significant security benefits, it’s important to understand its limitations:
Complexity: Managing a large number of users, roles, and permissions can become intricate, especially in large organizations. This can lead to errors and inconsistencies.
Rigidity: RBAC may not be ideal for highly dynamic environments where user permissions need frequent adjustments. The process of adding, removing, or modifying roles can be time-consuming.
Granularity: RBAC focuses on pre-defined roles, which might not perfectly align with every user’s needs. Achieving the right balance between granting sufficient access and maintaining security can be challenging.
User Management: RBAC relies heavily on accurate and up-to-date user data. Regular reviews and audits are essential to ensure continued effectiveness.
How Quloi Implements RBAC in it’s Supply Chain Collaboration Software
Quloi’s RBAC framework ensures that each user role in the supply chain can only access the information required to accomplish their tasks. For instance, buyers can view and manage purchasing orders and contract details, whereas forwarders have restricted access to track shipment statuses, view relevant shipping documentation, and manage logistics operations. This helps enhance data security and operational efficiency within the supply chain.
Streamlined Collaboration: The Quloi platform fosters collaboration between internal teams and external suppliers by granting relevant stakeholders appropriate access levels. This ensures that teams comply with standardized business practices and maintain data security.
Audit Trail and Compliance: Quloi facilitates regulatory compliance by maintaining a detailed audit trail of user activities within the platform. This ensures transparency, making it easier to demonstrate compliance during audits.
Data Security: Quloi restricts system access based on a user’s roles and permissions, reducing the risk of intentional or accidental data exposure.